“Three may keep a secret, if two of them are dead.” ―Benjamin Franklin
PowerShell Secrets, it's Uber Simple!
Overview
Creating a PowerShell script to automate a task saves us time and helps to reduce repetitive tasks. Scripts often connect multiple resources together, making them an easy pivot point for a bad actor. It may be tempting to include a password, API key, or secret in a PowerShell file, but this can easily turn a good script into a ticking time bomb. Luckily, PowerShell makes it easy to interact with secret vaults or even create one locally on any Windows, Linux or Mac device with the SecretManagement and SecretStore modules.
Getting Started
Installing the Modules
In order to setup the modules for the first time, run the following code in an administrative command prompt:
Install-Module Microsoft.PowerShell.SecretManagement, Microsoft.PowerShell.SecretStore
Create a Vault
Next, we will create a vault to hold our secrets. The easiest way to do this is to use the SecretStore vault, which creates a locally encrypted file. However, the SecretManagement utilities can also be connected to other more common vaults such as KeePass, LastPass, Azure KeyVault and Hashicorp Vault.
To do this, run the following command:
Register-SecretVault -Name KrabbyPattySecretFormula -ModuleName Microsoft.PowerShell.SecretStore -DefaultVault
Store a Secret
Now it is time to store our secret in the vault.
Set-Secret -Name Ingredients -Secret "Bun,Sea Cheese, Sea Lettuce, Sea Tomatoes, Pickles, Ketchup, Mustard, Mayonnaise, Sea Onions, Patty, Secret Sauce,Bun"
Enter and confirm a password to encrypt your vault. Try to use a long passphase and store it in a password manager for safe keeping!
Retrieve a Secret
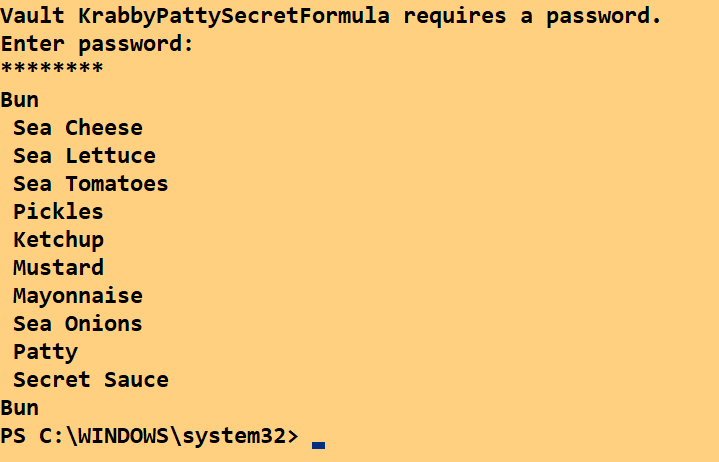
After the secret is placed into the vault, we can very easily retrieve it later in a script. Let’s list out all the ingredients in the Krabby Patty secret formula:
(Get-Secret -Name Ingredients -Vault KrabbyPattySecretFormula -AsPlainText).Split(',')
Putting it all Together
In order to unlock the vault we must provide the password interactively. This is obviously not possible during an automated process. The module provices a way to unlock the vault for a one hour period using the below command. It is important to securely store this password using an encrpted file, or ideally an environment variable in a CI/CD pipeline.
Unlock-SecretStore -Password $env:vaultPassword